- Password manager: Essential for businesses and individuals
- Password managers are no longer just password managers
Be aware of these domain impersonation techniques used by phishers!

We can't stop phishing, but we can educate ourselves to spot the phishing hooks.
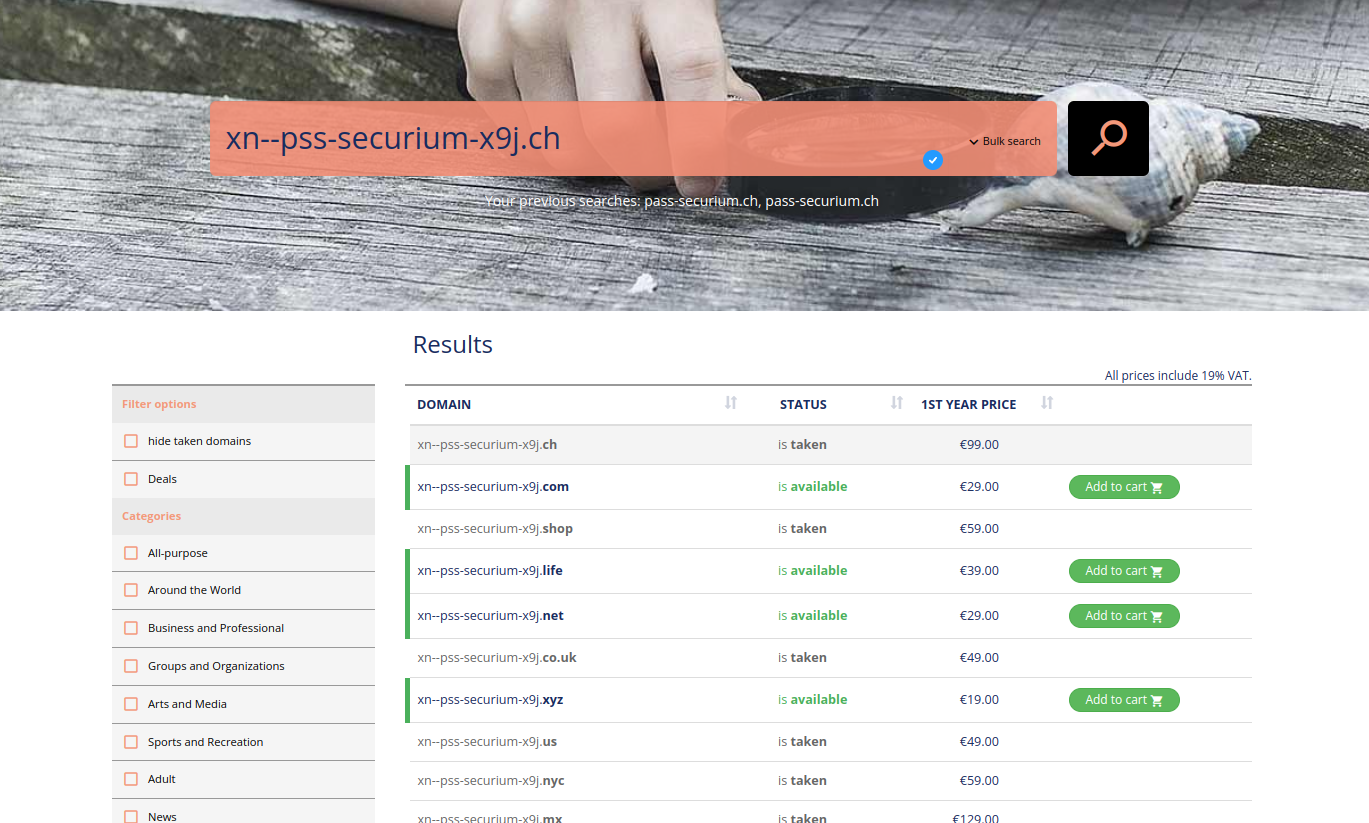
This article started when our security specialist came across a list of bought and sold domains (which looked strange at first glance) that could be displayed in browsers almost undistinguishable from our original domain.
This gibberish is called punicode, which used to be a serious phishing trick.
Punycode as an attack facilitator
Today, modern browsers such as Chrome, Firefox, Edge or Safari display the code and warn you when you follow a link with punycode that this may not be the domain you intended to visit.
Punycode is an encoding syntax used to represent Unicode characters (which include non-ASCII characters) in an ASCII-compatible encoding suitable for use in Domain Name System (DNS) lookups. It allows Internationalised Domain Names (IDNs) to be represented in the ASCII character set used by the DNS, allowing domain names to include characters from non-Latin scripts (e.g. Arabic, Cyrillic, Chinese).
Of course, this has not gone unnoticed by hackers and scammers. Punycode was (and is) used to register domains with Unicode characters that look like standard ASCII characters, facilitating phishing attacks. Browsers were used to decode Punycode back to Unicode, which could display deceptive domain names in the address bar.
Take a look at the example: on the left is the domain with punycode (hover over it to see how it's encoded), and on the right is our original domain.
pаss-securium.ch != pass-securium.ch
If they weren't next to each other, would you notice in your browser's address bar that the letter "a" is slightly different?
Fortunately, the punycode attack vector is now a thing of the past (unless, for some reason, you are using a very old browser version). But there are many more domain impersonation techniques that phishers can use to lure an unsuspecting user.
Domain impersonation
Domain impersonation is a tactic used by cybercriminals to deceive users by creating websites that closely resemble legitimate websites. The goal is to make people believe they are interacting with a trusted entity, facilitating phishing attacks, credential theft or malware distribution.
Let's look at other methods of domain impersonation:
Typosquatting (URL hijacking)
This technique involves attackers registering domain names that are common misspellings or typos of legitimate websites.
For example, instead of www.pass-securium.ch, they might use www.pas-securium.ch or www.pass-securum.ch.
As a result, users who mistype a URL may be redirected to malicious sites that mimic the legitimate site, potentially stealing sensitive information.
Homograph attacks
This type of domain impersonation uses homoglyphs - characters from different alphabets that are spelled exactly or almost exactly the same.
Attackers use characters that look similar to standard characters to create deceptive domain names.
For example, replacing the letter "o" with the number "0" (www.g00gle.com instead of www.google.com) can fool users who don't notice the subtle differences and may trust the malicious site.
Subdomain spoofing
This type of attack occurs when attackers create deceptive subdomains to make URLs appear legitimate.
For example, www.pass-securium.ch.login.example.com where the real domain is example.com.
Users may see familiar terms (e.g. "pass-securium.ch") in the URL and assume they're on a trusted site.
Misspelled subdomains
Attackers slightly change the subdomains of legitimate websites, e.g. www.secure-login.example.com vs. www.secure-logln.example.com (using "l" instead of "i").
Users may not notice the misspelling and trust the site.
Lookalike domains (combosquatting)
This is where phishing domains combine a legitimate brand name with additional words or characters.
For example: www.google-security.com or www.login-facebook.com. Such domains can trick users into thinking they're on a secure or official site associated with the legitimate site.
Top-level domain squatting
Our company officially owns the domains pass-securium.ch and .com, but not .net, .co.uk, .org, etc. Perhaps the problem of dubious entities buying branded domains with other top-level domains is not as acute for small brands, but users should be careful with well-known brands, especially during sales periods when discounts are used as bait.
HTTPS spoofing
Attackers obtain valid SSL certificates for spoofed domains in order to display the padlock icon.
For example, a malicious website www.fakebank.ch has an SSL certificate, so the browser displays it as secure, allowing users to trust the website because of the HTTPS indicator, even though the domain is fraudulent.
URL shortening and redirection
By using shortened URLs (e.g. bit.ly links) or redirection scripts to hide the actual destination, attackers can prevent users from seeing the final URL before clicking, increasing the risk of landing on a phishing site.
Mitigation and protection measures
1. Modern browsers have implemented safeguards:
- Display punycode domains in ASCII form: Suspicious domains can be displayed in their encoded punycode form to alert users (e.g. xn--...).
- Warning messages: Browsers can warn users when visiting potentially fraudulent sites.
2. User vigilance:
- Check URLs carefully, looking for unusual characters or inconsistencies.
- Avoid clicking on unverified links and be wary of links in emails or messages, especially from unknown sources.
- Use bookmarks to access frequently visited sites, rather than typing URLs
3. Security software:
- Anti-phishing tools: Install reputable security extensions or software that can detect and block known phishing sites.
- Use email services with strong spam and phishing detection capabilities.
4. Education and awareness:
- Keep up to date with common phishing techniques and scams.
- Organisations should train staff to recognise and report phishing attempts.
Conclusion
Domain impersonation remains a significant cybersecurity threat. Understanding the different techniques used by attackers is essential to recognising and preventing phishing attacks. By staying informed and taking proactive security measures, users and organisations can better protect themselves against these deceptive tactics.
If you have come across a site on the Internet that appears to impersonate our original site pass-securium.ch, please send us details by email, we will be very grateful!
Sources:
https://en.wikipedia.org/wiki/Punycode
https://www.youtube.com/watch?v=-8Gj26lKO24
https://www.jamf.com/blog/punycode-attacks/
https://krebsonsecurity.com/2018/03/look-alike-domains-and-visual-confusion/comment-page-1/